Classification of computer viruses
1. According to the parasitic method, it is divided into boot virus, file virus and mixed virus
Boot viruses refer to computer viruses that are parasitic in the disk boot area or main boot area. When this kind of virus uses the system to boot, it does not judge whether the content of the main boot area is correct or not. It invades the system in the process of guiding the system, resides in the memory, monitors the system operation, stands by for infection and destruction.
According to the parasitic position of the boot virus on the hard disk, it can be subdivided into the main boot record virus and the partition boot record virus. The main boot record virus infects the main boot area of ​​the hard disk, such as cannabis virus, 2708 virus, torch virus, etc .; the partition boot record virus infects the active partition boot record of the hard disk, such as small ball virus, Girl virus, etc.
File viruses refer to computer viruses that can parasitize in files. Such virus programs infect executable files or data files. Executable files such as 1575/1591 virus and 848 virus infect .COM and .EXE; macro viruses such as Macro / Concept and Macro / Atoms infect .DOC files.
The compound virus refers to a computer virus with a parasitic mode of a guided virus and a file virus. This virus expands the infection path of the virus program. It infects both the boot record of the disk and the executable file. When the disk infected with this virus is used to boot the system or call and execute the infected file, the virus will be activated. Therefore, when detecting and removing complex viruses, it is necessary to completely and thoroughly cure them. If only one characteristic of the virus is found, it is treated as a boot or file virus only. Although it seems to be removed, there are still hidden dangers. This disinfected "clean" system is even more aggressive. Such viruses include Flip virus, New World virus, One-half virus and so on.
According to the damage situation of computer virus (1) Benign computer virus Benign virus refers to that it does not contain the code that directly damages the computer system immediately. In order to show their existence, these viruses just spread non-stop and spread from one computer to another without destroying the data in the computer. Some people disagree with the infection of this type of computer virus and think that this is just a prank and it doesn't matter. In fact, both benign and malignant are relative. When a benign virus gains control of the system, it will reduce the operating efficiency of the entire system and reduce the total amount of available memory on the system, making certain applications inoperable. It also competes with the operating system and applications for control of the CPU, causing the entire system to deadlock from time to time, causing trouble for normal operation. Sometimes there will be several viruses cross-infected in the system, and a file is repeatedly infected by several viruses. For example, the original file with only 10KB becomes about 90KB, which means that it has been repeatedly infected dozens of times by several viruses. This not only consumes a large amount of valuable disk storage space, but the entire computer system also cannot work normally due to various viruses parasitic in it. Therefore, the damage caused by the so-called benign virus to the computer system cannot be underestimated (2) Malignant computer virus Malignant virus refers to the operation that damages and destroys the computer system in its code, and will directly damage the system when it is infected or attack effect. There are many such viruses, such as Michelangelo virus. When Mie virus occurs, the first 17 sectors of the hard drive will be completely destroyed, making the data on the entire hard drive unrecoverable, and the damage caused is irreversible. Some viruses will also format the hard disk and destroy it. These operating codes are intentionally written into viruses, which is one of its nature. Therefore, this type of malignant virus is very dangerous and should be guarded against. Fortunately, the anti-virus system can recognize the presence or absence of computer viruses by monitoring such abnormal actions in the system, or at least issue an alarm to alert the user.
According to the linking method of computer virus, because the computer virus itself must have an attack object to realize the attack on the computer system, the object attacked by the computer virus is the executable part of the computer system. (1) Source code virus The virus attacks a program written in a high-level language. The virus is inserted into the original program before the program written in the high-level language is compiled and becomes a part of a legal program. (2) Embedded virus This virus embeds itself into an existing program, linking the main program of the computer virus with its attack target in an inserted manner. This computer virus is difficult to write) Once it invades the program body, it is more difficult to eliminate. If polymorphic virus technology, super virus technology and covert virus technology are used at the same time, it will bring serious challenges to the current anti-virus technology.
(3) Shell-type virus The shell-type virus surrounds itself around the main program without modifying the original program. This virus is the most common, easy to write, and easy to find. The size of the general test file can be known.
(4) Operating system virus This virus uses its own program to join or replace part of the operating system to work, which is very destructive and can lead to the paralysis of the entire system. Dot virus and cannabis virus are typical operating system viruses. When this virus is running, it replaces the legal program module of the operating system with its own logical part. According to the characteristics of the virus and the status and role of the legal program module in the operating system being replaced in the operating system and the virus replacing the operating system Replace the method, etc. to destroy the operating system.
According to the system classification of computer virus attack 1) Viruses attacking DOS system. This type of virus appears the earliest and most, with the most variants. At present, computer viruses that appear in China are basically these types of viruses, which account for 99% of the total number of viruses. (2) Viruses that attack Windows systems. Since Windows' graphical user interface (GUI) and multi-tasking operating system are very popular with users, Windows is gradually replacing DOS and becoming the main target of virus attacks. The first CIH virus found to damage computer hardware is a Windows 95/98 virus. (3) Viruses that attack UNIX systems. Currently, UNIX systems are widely used, and many large operating systems use UNIX as their main operating system, so the emergence of UNIX viruses is also a serious threat to human information processing. (4) Viruses that attack OS / 2 systems. The first virus in the world to attack the OS / 2 system has been found. Although it is simple, it is also an ominous sign.
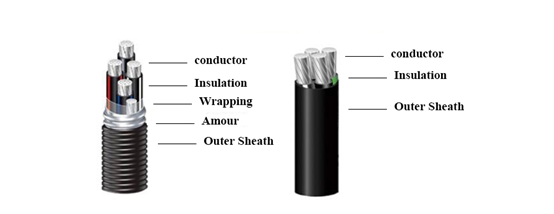
PVC Rare Earth Aluminum Alloy Power Cable is kind of cable, in which the rare earth high compressed aluminum alloy is used as conductor, and PVC is used as insulation and Jacket. It has completely independent intellectual property rights and removed the defects of aluminum cable systematically. It applies to both dry and moist places at the temperature of 75ºC and under, and the temperature of short circuit is 160ºC. The alloyed material greatly improves the toughness and high creep resistance. Due to its low density compared to copper wire and high strength, Aluminum Alloy Wire is preferred by customers.

Standard: GA306 Jacket: PVC
Conductor: aluminum alloy Cores: single core or multicores
Insulation: PVC Rated voltage: 0.6/1KV
Advantages:
- Conductor fatigue resistance
- Creep resistance
- Impact resistance
- Easy to bend
- Light weight
- Easy installation
- Long life span
- Flame retarded
- Fire resistant
- Zero halogen & low smoke
- Corrosion & abrasion resistant
- Decent mechanical strength
- Chemical & acid resistance
- ...
Application:
- Lighting
- High rising buildings
- Public Buildings
- Family residence
- Household appliances
- Electrical equipment
- Power console
- Automotive industry
- Government buildings
- Power transmission and distribution lines
- And many more...
Welcome to visit our factory to learn more about us. If you have any questions, please feel free to contact us.
PVC Insulated And Sheathed Alloy Cable
PVC Insulated And Sheathed Alloy Cable,PVC Insulated Alloy Cable,PVC Sheathed Alloy Cable,Insulated PVC Jacket Power Cable
Smartell Technology Co.,Ltd , http://www.liencable.com