Abstract: Based on the study of the principle and work of MPLS-based VPN technology, a network composition model of MPLS VPN based on BGP extension is given, and each device and its function in this model are also described. Finally, the technical advantages and application prospects of MPLS VPN are analyzed.
With the vigorous development of the Internet, people have put forward higher requirements for their applications. However, the Internet lacks effective traffic and network bandwidth management methods, and the network often blocks. There is no guarantee of quality of service (QoS), and many applications seem to be unable to cope with current IP technologies (such as voice and video). The emerging multi-protocol label switching technology (MPLS: MulTI Protocol Label Switching) is expected to solve this problem.
1 Introduction to VPN
VPN refers to the technology of relying on ISPs and other NSPs to establish proprietary data communication networks in public networks. In a virtual private network, the connection between any two nodes does not have the end-to-end physical link required by the traditional private network, but is dynamically formed using some public network resources. The VPN technology uses measures such as seasonal authentication, access control, confidentiality, and data integrity to ensure the confidentiality, integrity, and availability of information during transmission. It is a safe, reliable, convenient and fast private network for governments and enterprises on the public Internet, and can save money. VPN technology is the best solution for WAN construction. It will not only greatly save the cost of WAN construction and operation and maintenance, but also has the advantages of low cost of ownership, easy management, less overhead, high flexibility, and good confidentiality.
2 VPN technology based on MPLS
2.1 Basic principles of MPLS
MPLS VPN refers to a virtual private network built on the basis of MPLS technology, that is, using MPLS technology to build an enterprise IP private network on a public IP network to achieve multi-service broadband connections for data, voice, and images. And combined with different services, traffic engineering and other related technologies, to provide users with high-quality services. MPLS VPN can provide powerful QoS capabilities while providing all the functions of the original VPN network. It has the characteristics of high reliability, high security, strong expansion capabilities, flexible control strategies and powerful management capabilities.
MPLS is a special forwarding mechanism. It assigns labels to IP data packets entering the network, and forwards the IP data packets through the exchange of labels. The label exists as a substitute for the IP header in the network. Within the network, the path that MPLS passes through the data packet is forwarded by switching the label (instead of looking at the IP header); when the data packet is to exit the MPLS network, the data packet Unpack and continue to reach the destination according to the routing of IP packets. 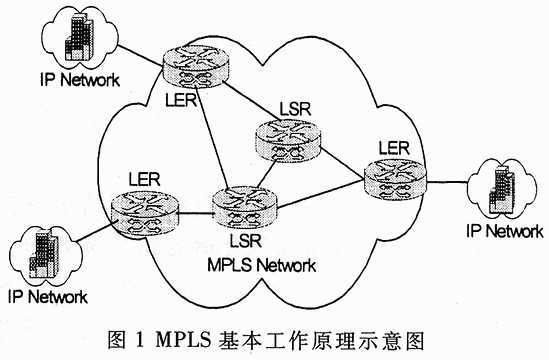
As shown in Figure 1, the MPLS network contains some basic elements. The node at the edge of the network is called the label edge router (LER: Label Edge Router), and the core node of the network is called the label switching router (LSR: Label Switching Router). LER nodes provide high-speed switching functions in the network. The path between MPLS nodes is called label switched path (LSP: Label Switched Path). An LSP can be regarded as a unidirectional tunnel running through the network.
The work flow of MPLS can be divided into three aspects: the edge behavior of the network, the central behavior of the network, and how to establish the label switching path.
1. Network edge behavior
When an IP packet reaches a LER, MPLS applies the label for the first time. First, LER must analyze the information in the IP header and distinguish it according to its destination address and service level.
In LER, MPLS uses the concept of Forwarding Equivalence Class (FEC: Forwarding Equivalence Class) to map the incoming data stream to an LSP. Simply put, FEC defines a group of data packets along the same path with the same processing. This means that all packets with the same FEC can be mapped to the same label.
For each FEC, LER establishes an independent LSP through the network to reach its destination. After the data packet is assigned to a FEC, LER can generate a label for it based on the label information base (LIB: Label InformaTIon Base). The label information base maps each FEC to the label of the next hop of the LSP. If the next hop link is ATM, MPLS will use the VCI in the ATM VCC as the label.
When forwarding a data packet, the LER checks the FEC in the label information base, and then encapsulates the data packet with the LSP label and sends it out from the next interface specified by the label information base.
2. The core behavior of the network
When a tagged packet arrives at the LSR, the LSR extracts the incoming tag and uses it as an index to search in the tag information base. When the LSR finds the relevant information, it takes out the outgoing mark and replaces the incoming mark with the outgoing mark, and sends the data packet from the next-hop interface described in the mark information database.
Finally, the data packet reaches the other end of the MPLS domain. At this point, the LER strips the encapsulated label and continues to transmit the data packet to the destination according to the routing of the IP packet.
3. How to establish a label switching path
There are two main ways to establish an LSP:
(1) "Hop by Hop (hop by hop)" routing
A Hop-by-Hop LSP is part of the IP tree from the source site to a specific destination site. For these LSPs, MPLS builds a set of trees by mimicking the destination-oriented way in which IP forwards packets.
From the perspective of traditional IP routing, each router along the way must check the destination address of the packet and select an appropriate path to send the packet out. This is not the case with MPLS. Although the data packet is also transmitted along the same path selected by the IP route, its data packet header is not checked from the beginning to the end of the entire path.
At each node, the tree generated by MPLS is generated by allocating labels for the next hop level by level, and by generating labels by exchanging labels with their peers. The exchange is completed through the request of the label distribution protocol (LDP: Label DistribuTIon Protocol) and the corresponding message.
(2) Explicit routing
The main advantage of MPLS is that it can use traffic to design "pilot" packets. MPLS allows network operators to determine an explicit routed LSP (ER-LSP) at the source node to specify the path the data packet will choose. ER-LSP establishes a direct end-to-end path from the source to the destination. MPLS embeds explicit routing into the information of the label distribution protocol that restricts routing, thereby establishing this path.
2.2 Basic MPLS VPN implementation
As shown in Figure 2, the MPLS Layer 3 VPN based on BGP extension contains the following basic components:
PE: Provider Edge Router. The PE router uses static routing, RIPv2, OSPF, or EBGP to exchange routing information with the CE router. Although the PE router maintains VPN routing information, it only needs to maintain VPN routes for those VPNs directly connected to it. Each PE router maintains a VRP (Virtual RouTIng Forwarding Table) for each site directly connected to it, and each client connection is mapped to a certain VRF. Learn the local VPN routing information from the CE router. PE routers use IBGP to exchange VPN routing information with other routers. The PE router can protect the IBGP session to the route reflector as an alternative to the full mesh IBGP session. When MPLS is used to forward VPN data traffic in the provider backbone, the ingress PE router is used as the ingress MPLS, and the ingress and egress PE router is used as the egress LSR. 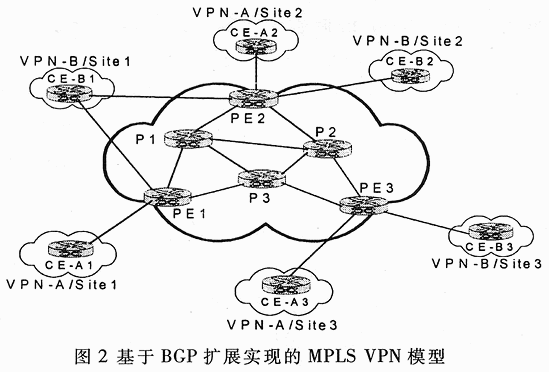
CE: Customer Edge (CE) equipment allows customers to access the service provider network through a data link that connects to one or more supplier edge (PE) routers. The CE device is an IP router, which establishes an adjacency relationship with the directly connected PE router. After establishing the adjacency, the CE router broadcasts the local VPN route of the site to the PE router, and learns the remote VPN route from the PE router.
Prouter: Provider Router, a provider router is any router in the provider network that is not connected to CE equipment. When forwarding VPN data traffic between PE routers, the provider router is used as the MPLS connection LSR. Since the traffic is forwarded in the MPLS backbone using a two-layer label stack, the supplier router only needs to maintain the route to the supplier PE router, and does not need to maintain the VPN routing information dedicated to each customer site.
RR: Route Reflector, BGP route reflector
ASBR: Automated System Border Router, an autonomous system border router, which exchanges VPN routes with other autonomous systems when implementing VPNs across autonomous systems.
MP-BGP: Multi-protocol extended BGP, which carries IPv4 / VPN routes that carry labels, including MP-IBGP and MP-EBGP.
PE-CE routing protocol: Pass user network routes between PE and CE, which can be static routes, or RIP, OSPF, ISIS, BGP protocols.
LDP: Label Distribution Protocol, establishes a best effort LSP between PEs. After P routers, all PEs and P routers need to be supported. RSVP-TE: When VPN needs QoS guarantee, establish ER-LSP with QoS capability between PEs.
VRF: Virtual Routing Fowarding Table, a virtual routing forwarding table, which contains routing tables, forwarding tables, interfaces (sub-interfaces), routing instances, and routing policies related to the same site. On the PE device, the physical port or logical port belonging to the same VPN corresponds to a VRF, which can be configured through the command line or network management tool. The main parameters include RD (Route Distinguish), Import Route-Targets, Export Route-Targets, interface (sub Interface) etc.
VPN user site: Site is an isolated IP network in VPN. Generally speaking, it does not pass through the backbone network. The company headquarters and branches are specific examples of Site. The CE router is usually a router or switching device in the VPN Site. The Site is connected to the PE device through a separate physical port or logical port (usually a VLAN port).
After users access the MPLS VPN, each site provides one or more CEs to connect to the PE of the backbone network, and configure VRF for the site on the PE, which will connect the physical interface, logical interface, and even L2TP / IPSec tunnel of the PE-CE It is bound to the VRF, but it cannot be a multi-hop Layer 3 connection.
The IPv4 address of the BGP NLRI extended by the MPLS VPN implemented by BGP extension adds an 8-byte RD (Route Distinguisher) before it to mark the VPN members (Site). Each VRF can be configured with certain policies, which stipulates which site routing information the VPN can receive and which site routing information can be advertised. The PE performs route calculation based on the information published by the BGP extension, and generates a routing table of the relevant VPN.
Generally, PE-CE exchanges routing information through static routes, and can also use RIP, OSPF, BGP, IS-IS and other protocols. Static routing can reduce the fluctuation of the backbone network BGP routes due to poor management of CE devices. , Thereby providing the stability of the backbone network.
MPLS BGP Layer 3 VPN is suitable for fixed Internet / Extranet users. Each site can represent the headquarters or branch of the Internet / Extranet. Only one physical or logical link is required between the CE and PE devices of the MPLS Layer 3 VPN, but the PE devices must store multiple routing tables. If a dynamic routing protocol is run between CPE or PE, the PE must also support multiple instances, which requires high PE performance. The BGP protocol needs to be run between PE and PE, which has poor scalability. Currently, one or more route reflectors can solve this problem. For VPNs in the same AS (Automated System) domain, you must establish a PE for the router's IBGP connection between operators, and establish an IBGP connection with the route reflector.
MPLS BGP Layer 3 VPN can configure some static routes with Internet routes to achieve VPN Internet access services, and can provide VPN interconnection for operators that belong to the same AS but have no backbone network across different regions. That is, to provide "operator's operator" mode VPN network interconnection.
2.3 Advantages of MPLS
1. High security. MPLS's Label Switching Path (LPS) has similar security to FR and ATM VCC; in addition. MPLS VPN also integrates IPSEC encryption, and at the same time, when users are transparent, users can use firewalls, data encryption and other methods to further improve security.
2. Powerful scalability. First, the number of VPNs that the network can accommodate is large; second, users of the same VPN are easy to expand.
3. Business integration capabilities. MPLS VPN provides the ability to integrate data, voice and video.
4. Flexible control strategy. Special control strategies can be formulated to meet the special needs of different users and realize value-added services.
5. Powerful management function. Adopt centralized management, unified platform for business configuration and scheduling, reducing the burden on users.
6. Service Level Agreement (SLA). At present, different services, flow control and service levels are used to ensure certain flow control. In the future, broadband guarantees and higher service quality guarantees can be provided.
7. Save costs for users.
MPLS is a new technology that combines the advantages of the link layer and the IP layer. Not only can VPN services be provided on the MPLS network, but services such as QoS, TE, and multicast can also be carried out. As MPLS applications continue to heat up, whether it is a product or a network, support for MPLS is no longer an additional requirement. Although VPN is a newly emerging comprehensive network technology, it has already shown its strong vitality. In China, where the network foundation is weak, the demand for IP virtual private networks by the government and enterprises is not high, but I believe that with the government's Internet access, especially driven by e-commerce, the solution of basic MPLS IP virtual private network technology is bound to be impossible Estimated market prospects.
Restaurant Pos,Restaurant Pos Software,Restaurant Billing Software Manufacturers and Suppliers in China
Increase Restaurant Upselling and Grow Revenue With Gmaii Restaurant Pos System
Could your restaurant use a boost in revenue? Would your servers like to be making more in tips? If you answered [yes" to either of these questions, you could benefit from adopting an easily implemented Gmaii Restaurant Pos System for your business.
You might be thinking that selling some [side fries" or getting a couple customers to [add bacon" isn`t going to do much for your revenue (or at least not enough to justify adopting a brand new POS). And if you were just making a couple of one-off upsells, then sure, you might be right.
Restaurant Pos System
Restaurant Pos,Restaurant Pos Software,Restaurant Billing Software,Best Pos System For Restaurant
Shenzhen Gmaii Technology Limited , https://www.gmaiipos.com